- User Account Has Expired Linux
- User Account Has Expired Pam
- Windows 10 Has Expired
- User's Account Has Expired Processmaker
- User Account Has Expired Suse
- User Account Has Expired Ad
Windows - Resolve 'The user's account has expired' when attempting to sign into the PC by Jeremy Canfield Updated: March 13th, 2020 Windows articles When attempting to sign into the PBI domain on any PC, message 'The user's account has expired' is displayed.
This article describes information about using the UserAccountControl attribute to manipulate user account properties.
Originally published July, 2017 and updated August, 2019. How to Get a List of Expired User Accounts with PowerShell. One of the most important tasks that an Active Directory administrator performs is ensuring that expired user accounts are reported in a timely manner and that action is taken to immediately remove or disable them. This hotfix does not provide a method for changing a password directly through Mstsc.exe for non-domain-joined clients. However, after you install this hotfix, users who try to log on to RDWeb (that is, on to the web portal itself) by using an account that has an expired password will be redirected to the password change page.
Press the Win+R keys to open Run, type lusrmgr.msc into Run, and click/tap on OK to open Local. The SQL user (the SQL login account which the Controller application server uses to connect to the database) has an expired password. More Information By default, when creating a new SQL login (on modern versions of SQL) several password options are enabled, for example.
User Account Has Expired Linux
Original product version: Windows Server 2012 R2
Original KB number: 305144
Summary
When you open the properties for a user account, click the Account tab, and then either select or clear the check boxes in the Account options dialog box, numerical values are assigned to the UserAccountControl attribute. The value that is assigned to the attribute tells Windows which options have been enabled.
To view user accounts, click Start, point to Programs, point to Administrative Tools, and then click Active Directory Users and Computers.
List of property flags
You can view and edit these attributes by using either the Ldp.exe tool or the Adsiedit.msc snap-in.
The following table lists possible flags that you can assign. You cannot set some of the values on a user or computer object because these values can be set or reset only by the directory service. Ldp.exe shows the values in hexadecimal. Adsiedit.msc displays the values in decimal. The flags are cumulative. To disable a user's account, set the UserAccountControl attribute to 0x0202 (0x002 + 0x0200). In decimal, this is 514 (2 + 512).
Note
You can directly edit Active Directory in both Ldp.exe and Adsiedit.msc. Only experienced administrators should use these tools to edit Active Directory. Both tools are available after you install the Support tools from your original Windows installation media.
| Property flag | Value in hexadecimal | Value in decimal |
|---|---|---|
| SCRIPT | 0x0001 | 1 |
| ACCOUNTDISABLE | 0x0002 | 2 |
| HOMEDIR_REQUIRED | 0x0008 | 8 |
| LOCKOUT | 0x0010 | 16 |
| PASSWD_NOTREQD | 0x0020 | 32 |
| PASSWD_CANT_CHANGE You cannot assign this permission by directly modifying the UserAccountControl attribute. For information about how to set the permission programmatically, see the Property flag descriptions section. | 0x0040 | 64 |
| ENCRYPTED_TEXT_PWD_ALLOWED | 0x0080 | 128 |
| TEMP_DUPLICATE_ACCOUNT | 0x0100 | 256 |
| NORMAL_ACCOUNT | 0x0200 | 512 |
| INTERDOMAIN_TRUST_ACCOUNT | 0x0800 | 2048 |
| WORKSTATION_TRUST_ACCOUNT | 0x1000 | 4096 |
| SERVER_TRUST_ACCOUNT | 0x2000 | 8192 |
| DONT_EXPIRE_PASSWORD | 0x10000 | 65536 |
| MNS_LOGON_ACCOUNT | 0x20000 | 131072 |
| SMARTCARD_REQUIRED | 0x40000 | 262144 |
| TRUSTED_FOR_DELEGATION | 0x80000 | 524288 |
| NOT_DELEGATED | 0x100000 | 1048576 |
| USE_DES_KEY_ONLY | 0x200000 | 2097152 |
| DONT_REQ_PREAUTH | 0x400000 | 4194304 |
| PASSWORD_EXPIRED | 0x800000 | 8388608 |
| TRUSTED_TO_AUTH_FOR_DELEGATION | 0x1000000 | 16777216 |
| PARTIAL_SECRETS_ACCOUNT | 0x04000000 | 67108864 |
Note
In a Windows Server 2003-based domain, LOCK_OUT and PASSWORD_EXPIRED have been replaced with a new attribute called ms-DS-User-Account-Control-Computed. For more information about this new attribute, see ms-DS-User-Account-Control-Computed attribute](/windows/win32/adschema/a-msds-user-account-control-computed).
Property flag descriptions
SCRIPT - The logon script will be run.
ACCOUNTDISABLE - The user account is disabled.
HOMEDIR_REQUIRED - The home folder is required.
PASSWD_NOTREQD - No password is required.
PASSWD_CANT_CHANGE - The user cannot change the password. This is a permission on the user's object. For information about how to programmatically set this permission, see Modifying User Cannot Change Password (LDAP Provider).
ENCRYPTED_TEXT_PASSWORD_ALLOWED - The user can send an encrypted password.
TEMP_DUPLICATE_ACCOUNT - This is an account for users whose primary account is in another domain. This account provides user access to this domain, but not to any domain that trusts this domain. This is sometimes referred to as a local user account.
NORMAL_ACCOUNT - This is a default account type that represents a typical user.
INTERDOMAIN_TRUST_ACCOUNT - This is a permit to trust an account for a system domain that trusts other domains.
WORKSTATION_TRUST_ACCOUNT - This is a computer account for a computer that is running Microsoft Windows NT 4.0 Workstation, Microsoft Windows NT 4.0 Server, Microsoft Windows 2000 Professional, or Windows 2000 Server and is a member of this domain.
SERVER_TRUST_ACCOUNT - This is a computer account for a domain controller that is a member of this domain.
DONT_EXPIRE_PASSWD - Represents the password, which should never expire on the account.
MNS_LOGON_ACCOUNT - This is an MNS logon account.
SMARTCARD_REQUIRED - When this flag is set, it forces the user to log on by using a smart card.
TRUSTED_FOR_DELEGATION - When this flag is set, the service account (the user or computer account) under which a service runs is trusted for Kerberos delegation. Any such service can impersonate a client requesting the service. To enable a service for Kerberos delegation, you must set this flag on the userAccountControl property of the service account.
NOT_DELEGATED - When this flag is set, the security context of the user is not delegated to a service even if the service account is set as trusted for Kerberos delegation.
USE_DES_KEY_ONLY - (Windows 2000/Windows Server 2003) Restrict this principal to use only Data Encryption Standard (DES) encryption types for keys.
DONT_REQUIRE_PREAUTH - (Windows 2000/Windows Server 2003) This account does not require Kerberos pre-authentication for logging on.
PASSWORD_EXPIRED - (Windows 2000/Windows Server 2003) The user's password has expired.
TRUSTED_TO_AUTH_FOR_DELEGATION - (Windows 2000/Windows Server 2003) The account is enabled for delegation. This is a security-sensitive setting. Accounts that have this option enabled should be tightly controlled. This setting lets a service that runs under the account assume a client's identity and authenticate as that user to other remote servers on the network.
PARTIAL_SECRETS_ACCOUNT - (Windows Server 2008/Windows Server 2008 R2) The account is a read-only domain controller (RODC). This is a security-sensitive setting. Removing this setting from an RODC compromises security on that server.
UserAccountControl values
These are the default UserAccountControl values for the certain objects:
- Typical user: 0x200 (512)
- Domain controller: 0x82000 (532480)
- Workstation/server: 0x1000 (4096)
Disabled accounts
If an organization has a provisioning process in place for governing (automatically) the enabling and disabling of account status and (or) there is a good frequency of guest / vendor engagement, this process is very effective. Owing to the uncertainty attached to such vendor engagement that has an uncertain expiry date, an automated process can’t be preset.
Also in a scenario where a vendor engagement needs to be controlled due to inactivity, the account can be disabled provisionally for security and can be re-enabled upon need.

A disabled account can be set at: Account -> Properties -> Account tab ->Account Options -> select checkbox “Account is disabled”

Locked accounts
An account can be locked automatically based on the organization’s Account Lockout Policy. Supposing such a process is not in place, the account could be compromised and proves fatal to the organizational data.
One must not trust the event logs wholly too. The logs are generated in large volumes and it is impossible to crack a potential breach from an account that does not conform to the Account Lockout Policy or to manually disable every single account for that matter.
The Account lockout threshold can be set at group policy: Computer Configuration -> Policies -> Windows Settings ->Security Settings -> Account Policy -> Account Lockout Policy.
User Account Has Expired Pam
Expired accounts
Windows 10 Has Expired
For organizations depending largely on contract-based assignments, this utility is a boon. The privilege of setting an account expiry time saves you the trouble of remembering and having to come back to it manually upon expiry. When the contract comes to an end, the account automatically expires thus providing no scope for security breaches. Also, if an account provisioning process is in place, this setting clearly adapts to suit it.
Expired account can be set at: Account -> Properties -> Account tab -> Account expires -> End of
Key difference after Status change:
All accounts behave similarly after the change except, the only difference being that of the locked accounts. Where, the account remains locked only for a specified duration and can be ‘automatically’ unlocked upon completion of the said duration. If duration is set to 0, it will never be ‘automatically’ unlocked.
Event ID in logon event.
2003:
531: Logon failure. A logon attempt was made using a disabled account.
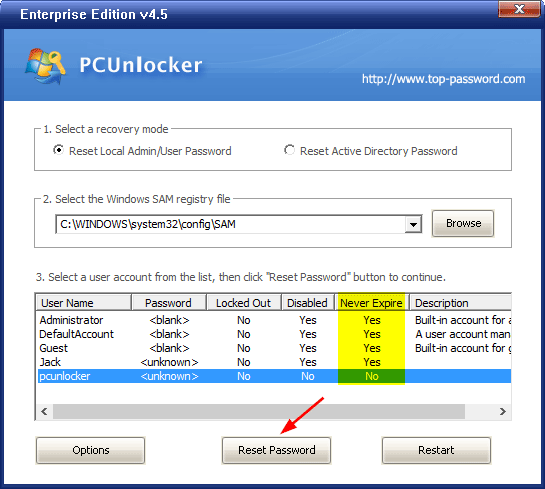
532: Logon failure. A logon attempt was made using an expired account.

User's Account Has Expired Processmaker
539: Logon failure. The account was locked out at the time the logon attempt was
made
2008:
The 2008 equivalent of ALL failed logon events is: “4625: An account failed to log on”
User Account Has Expired Suse
Failure reason: Same as above
Comments
User Account Has Expired Ad
comments